iw, wpa_supplicant, wpa_cli, hotstop, softap
wpa_passphrase
$ iwconfig
lo no wireless extensions.
wlan0 IEEE 802.11bgn Mode:Managed Access Point: Not-Associated
Tx-Power=0 dBm
Retry long limit:7 RTS thr:off Fragment thr:off
Encryption key:off
Power Management:off
sit0 no wireless extensions.
eth0 no wireless extensions.
# iwconfig
wlan1 no wireless extensions.
sit0 no wireless extensions.
p2p0 no wireless extensions.
dummy0 no wireless extensions.
wlan0 no wireless extensions.
lo no wireless extensions.
bridge0 no wireless extensions.
# iw dev wlan0 scan
# iwlist wlan0 scanning
wlan0 Interface doesn't support scanning.
# wpa_passphrase MUZICON > ./wpa_supplicant.conf2
암호입력
# cat wpa_supplicant.conf2
# reading passphrase from stdin
network={
ssid="입력한SSID"
#psk="입력된암호"
psk=06551ba75f139a78f3b19d28d87ac2260d869ed5ec444f2cf0d3f5f9e6aa15c1
}
생성된 파일에 추가 정보 입력
# reading passphrase from stdin
network={
ssid="입력한SSID"
#psk="입력된암호"
psk=06551ba75f139a78f3b19d28d87ac2260d869ed5ec444f2cf0d3f5f9e6aa15c1
priority=1
id_str="school"
}
$ wpa_cli -i wlan0 reconfigure 명령으로 인터페이스를 재설정합니다.
ssid가 ssid_name인 공유기에 연결한다
$ iwconfig wlan0 essid "ssid_name"
$ wpa_supplicant -iwlan0 -c /etc/wpa_supplicant/wpa_supplicant.conf &
wpa_supplicant -Dnl80211 -iwlan0 -c /etc/misc/wifi/wpa_supplicant.conf -B
ip를 dhcp로 할당 받는다
$ dhcpcd wlan0 &
sudo /usr/bin/dhcpcd -h computer --noipv4ll eth0
또는 수동으로 ip를 설정하려면
$ ifconfig wlan0 192.168.0.10 netmask 255.255.255.0 broadcast 192.168.0.255
$ route add default gw 192.168.0.1 wlan0
$ echo nameserver 192.168.0.1 > /etc/resolv.conf <--DNS 서버 설정
# iw reg get
global
country US: DFS-FCC
(2402 - 2472 @ 40), (N/A, 30), (N/A)
(5170 - 5250 @ 80), (N/A, 30), (N/A), AUTO-BW
(5250 - 5330 @ 80), (N/A, 24), (0 ms), DFS, AUTO-BW
(5490 - 5730 @ 160), (N/A, 24), (0 ms), DFS
(5735 - 5835 @ 80), (N/A, 30), (N/A)
(5842 - 5863 @ 5), (N/A, 30), (N/A)
(5850 - 5870 @ 10), (N/A, 30), (N/A)
(5860 - 5880 @ 10), (N/A, 30), (N/A)
(5865 - 5885 @ 20), (N/A, 30), (N/A)
(5870 - 5890 @ 10), (N/A, 30), (N/A)
(5880 - 5900 @ 10), (N/A, 30), (N/A)
(5890 - 5910 @ 10), (N/A, 30), (N/A)
(5895 - 5915 @ 20), (N/A, 30), (N/A)
(5900 - 5920 @ 10), (N/A, 30), (N/A)
(5910 - 5930 @ 10), (N/A, 30), (N/A)
(57240 - 70200 @ 2160), (N/A, 40), (N/A)
phy#1 (self-managed)
country US: DFS-FCC
(2402 - 2472 @ 40), (6, 30), (N/A)
(5170 - 5250 @ 80), (6, 24), (N/A)
(5250 - 5330 @ 80), (6, 24), (0 ms), DFS
(5490 - 5730 @ 160), (6, 24), (0 ms), DFS
(5735 - 5835 @ 80), (6, 30), (N/A)
default gateway 설정에 관한것
ip -4 addr flush dev $dev $label
ip route add {NETWORK/MASK} via {GATEWAYIP}
ip route add {NETWORK/MASK} dev {DEVICE}
ip route add default {NETWORK/MASK} dev {DEVICE}
ip route add default {NETWORK/MASK} via {GATEWAYIP}
ex)
# ip route add 172.10.1.0/24 via 10.0.0.100 dev eth0
Verify it:
# ip r
192.168.1.0/24 dev wlan0 proto kernel scope link src 192.168.1.1
192.168.225.0/24 dev bridge0 proto kernel scope link src 192.168.225.1
# ip link set dev tun0 up mtu 1500
# ip addr add dev tun0 10.8.0.2/24 broadcast 10.8.0.255
# ip route add 139.59.2.125/32 via 192.168.2.254
# ip route add 0.0.0.0/1 via 10.8.0.1
# ip route add 128.0.0.0/1 via 10.8.0.1
테스크탑에서 해봄
$ ip r
default via 172.26.32.1 dev eno1 proto static metric 100
169.254.0.0/16 dev eno1 scope link metric 1000
172.17.0.0/16 dev docker0 proto kernel scope link src 172.17.0.1 linkdown
172.26.32.0/22 dev eno1 proto kernel scope link src 172.26.35.72 metric 100
$ netstat -r
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
default 172.26.32.1 0.0.0.0 UG 0 0 0 eno1
link-local * 255.255.0.0 U 0 0 0 eno1
172.17.0.0 * 255.255.0.0 U 0 0 0 docker0
172.26.32.0 * 255.255.252.0 U 0 0 0 eno1
영구적으로 지정하기
# vim /etc/sysconfig/network-scripts/route-eth0
Append the following text:
172.10.1.0/24 via 10.0.0.100 dev eth0
wpa_supplicant.conf
scan_freq=2412 2437 2462 # 스캔을 이 대역에 제한
freq_list=5180 # 접속을 이 대역에 제
network={
key_mgmt=NONE
}
vi system/etc/wifi/wpa_supplicant.conf
ctrl_interface=DIR=/data/system/wpa_supplicant GROUP=system
update_config=1
network={
ssid="MUZICON"
key_mgmt=WPA-PSK
proto=WPA WPA2
pairwise=CCMP TKIP
group=CCMP TKIP WEP104 WEP40
psk="babobabo"
}
freq_list=2412 2417 2422 2427 2432 2437 2442 2447 2452 2457 2462 5180 5200 5220 5240 5260 5280 5300 5 320 5745 5765 5785 5805 5825
network={
ssid="linksys"
psk="some psk"
key_mgmt=WPA-PSK
disabled=1
}
# mount -o rw,remount /
# vi /etc/misc/wifi/wpa_supplicant.conf 를 열어서
network={
ssid="MUZICON"
key_mgmt=WPA-PSK
psk="passwd"
}
# wpa_supplicant -Dnl80211 -iwlan0 -c /home/apps/hohoho/wpa_supplicant.conf2 -B
# wpa_supplicant -Dnl80211 -iwlan0 -c /etc/misc/wifi/wpa_supplicant.conf -B
# dhcpcd wlan0
# adk-message-send 'connectivity_wifi_enable {set:true}'
# adk-message-send 'connectivity_wifi_connect {ssid:"MUZICON", password:"passwd"}'
DESCRIPTION
Iwlist is used to display some additional information from a wireless network interface that is not displayed by iwconfig(8). The main argument is used to select a category of information, iwlist displays in detailed form all information related to this category, including information already shown by iwconfig(8).
PARAMETERS
scan[ning]Give the list of Access Points and Ad-Hoc cells in range, and optionally a whole bunch of information about them (ESSID, Quality, Frequency, Mode...). The type of information returned depends on what the card supports.
Triggering scanning is a privileged operation (root only) and normal users can only read left-over scan results. By default, the way scanning is done (the scope of the scan) is dependant on the card and card settings.
This command takes optional arguments, however most drivers will ignore those. The option essid is used to specify a scan on a specific ESSID. With some card/driver, this enables to see hidden networks. The option last does not trigger a scan and read left-over scan results.freq[uency]/channelGive the list of available frequencies in the device and the number of defined channels. Please note that usually the driver returns the total number of channels and only the frequencies available in the present locale, so there is no one-to-one mapping between frequencies displayed and channel numbers.rate/bit[rate]List the bit-rates supported by the device.keys/enc[ryption]List the encryption key sizes supported and list all the encryption keys set in the device.powerList the various Power Management attributes and modes of the device.txpowerList the various Transmit Powers available on the device.retryList the transmit retry limits and retry lifetime on the device.ap/accesspoint/peersGive the list of Access Points in range, and optionally the quality of link to them. This feature is obsolete and now deprecated in favor of scanning support (above), and most drivers don't support it.
Some drivers may use this command to return a specific list of Peers or Access Points, such as the list of Peers associated/registered with the card. See your driver documentation for details.eventList the wireless events supported by the device.authList the WPA authentication parametes curently set.wpa[keys]List all the WPA encryption keys set in the device.genieList the Generic Information Elements set in the device (used for WPA support).modu[lation]List the modulations supported by the device and the modulations currently enabled.--versionDisplay the version of the tools, as well as the recommended and current Wireless Extensions version for the tool and the various wireless interfaces.--helpDisplay short help message.
FILES
SEE ALSO
iwconfig(8), iwspy(8). iwevent(8), iwpriv(8), wireless(7).
|
1. 개요 |
새로운 컴퓨터 또는 보드를 구매하였을 시 아래와 같은 현상이 발생하였을 때 해결 방법입니다.
1. WIFI가 연결되지 않는다.
2. WIFI 어뎁터(인터페이스)를 찾지 못한다.
3. 공유기(AP)를 찾지 못한다.
4. WIFI 사용하지 못한다.
|
2. 순서 |
1. 현재 동작 가능한 WIFI Adapters를 찾습니다.
|
1 |
iw dev |
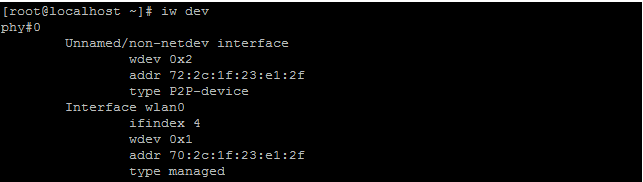
2. '1'번에서 찾은 WIFI Adapter 중 사용할 Adapter의 상태를 확인합니다. 저 같은 경우 아래 사진을 보면 알 수 있듯이 'state DORMANT' 라고 표시되고 있습니다. 꺼저있는 분들은 'state DOWN' 이라고 표시될 것입니다.
|
1 |
ip link show wlan0 |

3. 사용할 WIFI Adapter(Interface)를 동작시킵니다.
|
1 |
ip link set wlan0 up |
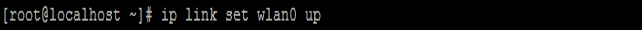
4. 다시 WIFI Adapter 중 사용할 Adapter의 상태를 확인합니다. 저 같은 경우 아래 사진을 보면 알 수 있듯이 'state DORMANT' 라고 표시되고 있습니다. 정삭적으로는 'state UP'이라고 표시될 것입니다.
|
1 |
ip link show wlan0 |
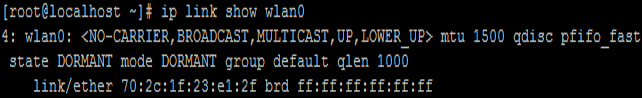
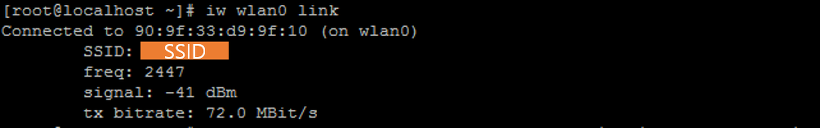
5. WIFI Adapter(Interface) 연결 상태를 확인합니다.
|
1 |
iw wlan0 link |

이후 부터는 공유기(AP)에 접속하는 과정입니다.
접속 방법은 여러가지가 있으며 connmanctl로 연결하는 법은
http://twinw.tistory.com/174에 설명되어 있습니다.
6. 주위 AP를 검색합니다. 검색하는 커맨드는 여러가지 있습니다.
|
1 |
iw wlan0 scan |
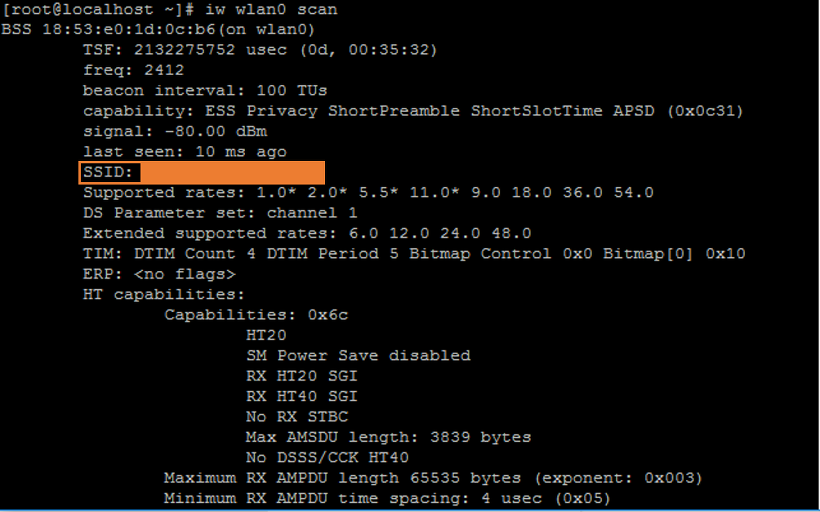
7. 연결할 AP의 SSID와 Passwd를 등록합니다.
|
1 2 3 |
wpa_passphrase SSID >> /etc/wpa_supplicant/wpa_supplicant.conf > Passwd cat /etc/wpa_supplicant/wpa_supplicant.conf |

8. WPA/WPA2 WIFI만 추가적으로 설정을 합니다.
* -B : Background에서 wpa_supplicant를 동작시킵니다.
* -D : 무선 드라이버를 지정합니다. wext는 일반 드라이버입니다.
* -c : 파일 경로입니다.
|
1 |
wpa_supplicant -B -D wext -i wlan0 -c /etc/wpa_supplicant/wpa_supplicant.conf |

9. SSID 연결 상태를 확인합니다. 만약 연결이 안되어있다면 재부팅을 합니다.
|
1 2 3 |
iw wlan0 link reboot iw wlan0 link |
10. dhclint로 부터 IP를 할당 받습니다. 한번씩
|
1 |
dhclient wlan0 |

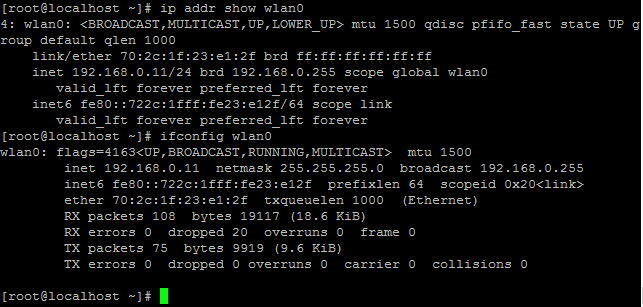
11. 할당된 ip를 확인합니다. 'dhclient wlan0' 커맨드 이후 바로 확인하시면 한번씩 IP를 할당받지 못할때가 있습니다. 이때는 재부팅을 해줍니다.
|
1 2 |
ip addr show wlan0 ifconfig wlan0 |
|
3. 참조 |
wpa_cli 사용
# wpa_cli
wpa_cli v2.3-5.1.1
Copyright (c) 2004-2014, Jouni Malinen <j@w1.fi> and contributors
This software may be distributed under the terms of the BSD license.
See README for more details.
Using interface 'wlan0'
Interactive mode
> list_network
network id / ssid / bssid / flags
>
> status
p2p_device_address=0e:1c:20:00:00:0c
p2p_state=IDLE
wifi_display=1
ifname=p2p0
address=0e:1c:20:00:00:0c
ifname=wlan0
address=0c:1c:20:00:00:0c
> help
commands:
status [verbose] = get current WPA/EAPOL/EAP status
ifname = get current interface name
ping = pings wpa_supplicant
relog = re-open log-file (allow rolling logs)
note = add a note to wpa_supplicant debug log
mib = get MIB variables (dot1x, dot11)
help [command] = show usage help
interface [ifname] = show interfaces/select interface
level = change debug level
license = show full wpa_cli license
quit = exit wpa_cli
set = set variables (shows list of variables when run without arguments)
get = get information
logon = IEEE 802.1X EAPOL state machine logon
logoff = IEEE 802.1X EAPOL state machine logoff
pmksa = show PMKSA cache
pmksa_flush = flush PMKSA cache entries
reassociate = force reassociation
reattach = force reassociation back to the same BSS
preauthenticate = force preauthentication
identity = configure identity for an SSID
password = configure password for an SSID
new_password = change password for an SSID
pin = configure pin for an SSID
otp = configure one-time-password for an SSID
passphrase = configure private key passphrase
for an SSID
sim = report SIM operation result
bssid = set preferred BSSID for an SSID
blacklist = add a BSSID to the blacklist
blacklist clear = clear the blacklist
blacklist = display the blacklist
log_level [] = update the log level/timestamp
log_level = display the current log level and log options
list_networks = list configured networks
select_network = select a network (disable others)
enable_network = enable a network
disable_network = disable a network
add_network = add a network
remove_network = remove a network
set_network = set network variables (shows
list of variables when run without arguments)
get_network = get network variables
dup_network = duplicate network variables
list_creds = list configured credentials
add_cred = add a credential
remove_cred = remove a credential
set_cred = set credential variables
get_cred = get credential variables
save_config = save the current configuration
disconnect = disconnect and wait for reassociate/reconnect command before
connecting
reconnect = like reassociate, but only takes effect if already disconnected
scan = request new BSS scan
scan_results = get latest scan results
bss < | > = get detailed scan result info
get_capability <eap/pairwise/group/key_mgmt/proto/auth_alg/channels/freq/modes> = get capabilies
reconfigure = force wpa_supplicant to re-read its configuration file
terminate = terminate wpa_supplicant
interface_add
= adds new interface, all parameters but
are optional
interface_remove = removes the interface
interface_list = list available interfaces
ap_scan = set ap_scan parameter
scan_interval = set scan_interval parameter (in seconds)
bss_expire_age = set BSS expiration age parameter
bss_expire_count = set BSS expiration scan count parameter
bss_flush = set BSS flush age (0 by default)
stkstart = request STK negotiation with
ft_ds = request over-the-DS FT with
wps_pbc [BSSID] = start Wi-Fi Protected Setup: Push Button Configuration
wps_pin [PIN] = start WPS PIN method (returns PIN, if not hardcoded)
wps_check_pin = verify PIN checksum
wps_cancel Cancels the pending WPS operation
wps_nfc [BSSID] = start Wi-Fi Protected Setup: NFC
wps_nfc_config_token <WPS|NDEF> = build configuration token
wps_nfc_token <WPS|NDEF> = create password token
wps_nfc_tag_read = report read NFC tag with WPS data
nfc_get_handover_req = create NFC handover request
nfc_get_handover_sel = create NFC handover select
nfc_report_handover = report completed NFC handover
wps_reg = start WPS Registrar to configure an AP
wps_ap_pin [params..] = enable/disable AP PIN
wps_er_start [IP address] = start Wi-Fi Protected Setup External Registrar
wps_er_stop = stop Wi-Fi Protected Setup External Registrar
wps_er_pin = add an Enrollee PIN to External Registrar
wps_er_pbc = accept an Enrollee PBC using External Registrar
wps_er_learn = learn AP configuration
wps_er_set_config = set AP configuration for enrolling
wps_er_config = configure AP
wps_er_nfc_config_token <WPS/NDEF> = build NFC configuration token
ibss_rsn = request RSN authentication with in IBSS
sta = get information about an associated station (AP)
all_sta = get information about all associated stations (AP)
deauthenticate = deauthenticate a station
disassociate = disassociate a station
chan_switch [sec_channel_offset=] [center_freq1=] [center_freq2=] [bandwidth=] [blocktx] [ht|vht] = CSA parameters
suspend = notification of suspend/hibernate
resume = notification of resume/thaw
roam = roam to the specified BSS
p2p_find [timeout] [type=*] = find P2P Devices for up-to timeout seconds
p2p_stop_find = stop P2P Devices search
p2p_connect <"pbc"|PIN> [ht40] = connect to a P2P Device
p2p_listen [timeout] = listen for P2P Devices for up-to timeout seconds
p2p_group_remove = remove P2P group interface (terminate group if GO)
p2p_group_add [ht40] = add a new P2P group (local end as GO)
p2p_prov_disc = request provisioning discovery
p2p_get_passphrase = get the passphrase for a group (GO only)
p2p_serv_disc_req = schedule service discovery request
p2p_serv_disc_cancel_req = cancel pending service discovery request
p2p_serv_disc_resp
p2p_set = set a P2P parameter
p2p_flush = flush P2P state
p2p_cancel = cancel P2P group formation
p2p_unauthorize = unauthorize a peer
p2p_presence_req [ ] [ ] = request GO presence
p2p_ext_listen [ ] = set extended listen timing
p2p_remove_client <address|iface=address> = remove a peer from all groups
wfd_subelem_set [contents] = set Wi-Fi Display subelement
wfd_subelem_get = get Wi-Fi Display subelement
fetch_anqp = fetch ANQP information for all APs
stop_fetch_anqp = stop fetch_anqp operation
interworking_select [auto] = perform Interworking network selection
interworking_connect = connect using Interworking credentials
anqp_get [,]... = request ANQP information
gas_request [QueryReq] = GAS request
gas_response_get
sudo apt-get install iw hostapd iptables udhcpd udhcpc macchanger
sudo -H gedit /etc/hostapd.conf /etc/udhcpd.conf /etc/default/udhcpd /etc/wpa_supplicant.conf
- hostapd.conf 내용
interface=wlan0
driver=nl80211
ssid=my_wifi_hotspot #Change the ssid name as you wish
channel=11 #I sugest you to use the same channel as your wireless network
hw_mode=g
wme_enabled=1
macaddr_acl=0
auth_algs=1
ignore_broadcast_ssid=0
country_code=US
wpa=3
wpa_passphrase=1234567890 #Change the passphrase as you wish
wpa_key_mgmt=WPA-PSK
wpa_pairwise=TKIP
rsn_pairwise=CCMP
wmm_enabled=0
ctrl_interface=/var/run/hostapd
ctrl_interface_group=0
ssid=SSID
- udhcpd.conf 내용
start 192.168.0.102 #These IPs must to be in the same subset as your current default route
end 192.168.0.117
interface new1
opt dns 192.168.0.1 #Your current default route (Gateway)
option subnet 255.255.255.0
opt router 192.168.0.101 #This IP must to be in the same subset as your current default route
option domain localhost
----
#!/bin/bash
service network-manager stop
sleep 1
pkill -15 nm-applet
sleep 1
ifconfig wlan0 down #wlan0 - the name of your wireless adapter
sleep 1
iw phy phy0 interface add new0 type station
iw phy phy0 interface add new1 type __ap
sleep 2
ifconfig new0 down
macchanger --mac 00:11:22:33:44:55 new0
ifconfig new1 down
macchanger --mac 00:11:22:33:44:66 new1
ifconfig new0 up
ifconfig new1 up
ifconfig new1 192.168.0.101 up #192.168.0.101 - the same IP defined for router in 'udhcpd.conf' file
hostapd /etc/hostapd.conf &
sleep 2
service udhcpd start
wpa_supplicant -inew0 -c/etc/wpa_supplicant.conf &
sleep 10
udhcpc -i new0
echo "1" > /proc/sys/net/ipv4/ip_forward
iptables --table nat --append POSTROUTING --out-interface new0 -j MASQUERADE
iptables --append FORWARD --in-interface new1 -j ACCEPT
------
default gateway 보는 방법
방법 1: route
[root@zetawiki ~]# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
172.27.0.0 * 255.255.0.0 U 0 0 0 eth0
link-local * 255.255.0.0 U 1002 0 0 eth0
default 172.27.0.1 0.0.0.0 UG 0 0 0 eth0
→ 이더넷 인터페이스는 1개(eth0)이며, 게이트웨이는 172.27.0.1
방법 2: netstat
[root@zetawiki ~]# netstat -r
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
172.27.0.0 * 255.255.0.0 U 0 0 0 eth0
link-local * 255.255.0.0 U 0 0 0 eth0
default 172.27.0.1 0.0.0.0 UG 0 0 0 eth0
→ 이더넷 인터페이스는 1개(eth0)이며, 게이트웨이는 172.27.0.1
방법 3: ip
root@zetawiki:~# ip route
default via 172.27.0.1 dev eth0
172.27.0.0/16 dev eth0 proto kernel scope link src 172.27.0.123
라우팅 테이블 확인
#route -n
라우팅 정보추가
#route add -net (네트워크주소) netmask(넷마스크값) dev(인터페이스 이름)
라우팅 정보삭제
#route del -net (네트워크주소) netmask(넷마스크값) dev(인터페이스 이름)
기본 게이트웨이 추가
#route add default gw(기본게이트웨이 주소) dev(인터페이스 이름)
기본 게이트웨이 삭제
#route del default gw(기본게이트웨이 주소) dev(인터페이스 이름)
라우팅 테이블에 막힌 ip풀어주기
#route del -host 해당ip reject
U : 경로가 유효한 상태라는 의미입니다.
G : 해당하는 경로가 gateway(대부분 라우터)를 향하고 있다는 의미입니다.
즉 그 네트워크로 가려면 라우터를 통과해야 도달할 수 있다는 의미입니다.
H : 이것은 호스트를 향하고 있다는 의미입니다. 즉 IP Address가 호스트를 뜻한다는 말입니다. 이 Flag가 없으면 그것은 네트워크를 의미한다는 말입니다.
약간의 부연 설명을 하자면 G Flag가 표시된것은 라우터를 거쳐서 간다는 의미이고, G Flag가 없다는 말은 직접 갈수 있는 경로(로컬)가 된다는 걸 의미하죠. 그것은 호스트일수도 있고, 네트워크 일수도 있습니다. IP Address가 네트워크 ID부분과 호스트 ID의 부분으로 이루어져 있다는 것은 아시죠?
H Flag는 호스트를 의미하고, H Flag가 없다면 그것은 네트워크라는 의미입니다.
예를 들자면 현재 경로가 유효하고 라우터를 거쳐야 갈 수 있는 외부의 호스트는
UGH 로 표시가 되겠죠?
예> netstat -rn
[3384:RG]# netstat -rn
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
0.0.0.0 56.1.1.1 0.0.0.0 UG 0 0 0 wanbridge
56.1.1.0 0.0.0.0 255.255.255.0 U 0 0 0 wanbridge
172.31.255.0 0.0.0.0 255.255.255.0 U 0 0 0 privbr
192.168.0.0 0.0.0.0 255.255.255.0 U 0 0 0 br0
192.168.100.1 0.0.0.0 255.255.255.255 UH 0 0 0 privbr
= [Route] Metric
The flags
Following is the list of flags and their significance in the routing table :
U : This flag signifies that the route is up
G : This flag signifies that the route is to a gateway. If this flag is not present then we can say that the route is to a directly connected destination
H : This flag signifies that the route is to a host which means that the destination is a complete host address. If this flag is not present then it can be assumed that the route is to a network and destination would be a network address.
D : This flag signifies that this route is created by a redirect.
M : This flag signifies that this route is modified by a redirect.
Direct route, Indirect route and the ‘G’ flag
A direct route is the one where the destination is directly connected to the forwarding host while in case of an indirect route the destination host is not directly connected to the forwarding host.
On a direct route the destination IP address and the link layer address in the datagram are that of the destination host while in case of an indirect route, the destination IP in the datagram remains unchanged but the link layer address changes to that of the next router to which this datagram is being delivered.
This is where the ‘G’ flag comes in handy. The ‘G’ flag above signifies that this is an indirect route. For a direct route, the ‘G’ flag is not set.
The ‘G’ flag Vs the ‘H’ flag
Now as we all know that the ‘G’ flag signifies the route. The route could be direct or indirect as explained above.
But the ‘G’ flag should not be confused by the ‘H’ flag. This flag signifies that the destination address in the entry is a host address or a network address.
As already discussed in the previous part of this article series, when the destination IP address from the received datagram is searched in the routing table the first the complete address is matched.
If complete address matching fails then the network ID is matched to see if the routing table has an entry for a network to which the destination IP address of the datagram belongs.
So we see that in case of a complete IP address match the entry would contain ‘H’ flag while in case of network ID match the entry would not contain the ‘H’ flag.
dhcp-client-script
$ iw reg set CN
$ iw reg get (./kernel/net/wirless/db.txt
$ iwpriv wlan0 getChannelList
$ wpa_cli -i wlan0 driver COUNTRY CN
'Linux' 카테고리의 다른 글
| make (0) | 2019.06.21 |
|---|---|
| zynq boot args (0) | 2019.05.21 |
| inittab respawn (0) | 2019.04.17 |



